 Office 365 has dozens of productivity-boosting tools that it can sometimes be difficult to keep up with all of them. One you may have overlooked is MyAnalytics, a machine learning-based tool to help you get more out of your employees’ work day.
Office 365 has dozens of productivity-boosting tools that it can sometimes be difficult to keep up with all of them. One you may have overlooked is MyAnalytics, a machine learning-based tool to help you get more out of your employees’ work day.
What is MyAnalytics?
MyAnalytics apply machine learning technology to your employees’ Office 365 data. By utilizing extremely powerful computing processes to analyze huge blocks of information, MyAnalytics can uncover trends and correlations that may be too complex for human discovery.
Every day, Office 365 users create several thousand new data points across Microsoft’s productivity suite, and there’s a lot of potential to rearrange meetings, project goals, and employee tasks to increase efficiency.
The most obvious improvement is with Outlook calendar. MyAnalytics tracks how much time you’re spending with each person in your office as well as the time you’re investing in specific projects. After sufficient information has been gathered, your Office 365 dashboard will begin coaching you on how to organize meetings and project goals based on your habits and past successes.
How can it improve your office?
Have you ever worked on a huge project that required multiple contributors? Did you all meet regularly to update each other? Users who add contacts — from both inside the company and out — and projects to MyAnalytics get reminders to stay in touch with co-workers most vital to project completion.
Every metric tracked by MyAnalytics can be shared with your team to make sure everyone is on the same page. So MyAnalytics is more than just a motivational tool, because sharing these metrics allows your team to identify bottlenecks and trends to smoothen the workflow process.
Response time is another key metric your employees are probably only vaguely aware of. MyAnalytics calculates average email response times — both from you and from contacts — to identify what time of day you’re best at communicating, and how you can adapt your schedule to get more work done in the same amount of time.
Privacy concerns
One of the greatest things about MyAnalytics is that it doesn’t introduce any new privacy concerns for business owners. All the data it uses to create customized coaching and advice is publicly available to everyone at your business — via calendar appointments, email content, and message timestamps. The only difference is that Microsoft is lending you the previously prohibitive computing power to sift through all of it.
Availability
This wonderful new tool comes with any Enterprise E5 plan, but can also be added on to E1 and E3 Enterprise plans for just a few dollars per month.
Increasing employee productivity is never as clear cut as it is with MyAnalytics. Install a solution, follow its advice, and start brainstorming about what to do with all your extra time. We’ve got plenty of other great solutions for streamlining your business processes — call us today to find out!

 Installing software that immediately boosts employee efficiency is any small- or medium-sized business owner’s dream. With Office 365’s dashboard, that’s exactly what you’re getting. And best of all, it’s directly integrated with your existing productivity suite. Read on to learn more.
Installing software that immediately boosts employee efficiency is any small- or medium-sized business owner’s dream. With Office 365’s dashboard, that’s exactly what you’re getting. And best of all, it’s directly integrated with your existing productivity suite. Read on to learn more. Machine learning is all the rage nowadays, and few vendors are providing as many solutions powered by this new technology as Microsoft does. Office 365 includes “intelligent” functionality for analyzing your employees’ time and coaching them on how to use it more efficiently.
Machine learning is all the rage nowadays, and few vendors are providing as many solutions powered by this new technology as Microsoft does. Office 365 includes “intelligent” functionality for analyzing your employees’ time and coaching them on how to use it more efficiently.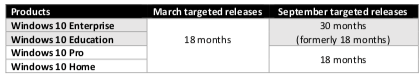
 Phishing scams disguise malicious links and emails as messages from trusted sources. The most recent scam to watch out for almost perfectly imitates a trusted invitation to collaborate through Microsoft SharePoint. It’s a three-step attack that’s easy to avoid if you know how it works.
Phishing scams disguise malicious links and emails as messages from trusted sources. The most recent scam to watch out for almost perfectly imitates a trusted invitation to collaborate through Microsoft SharePoint. It’s a three-step attack that’s easy to avoid if you know how it works. Have you ever received an email that claimed to come from a bank or government office when it obviously didn’t? It was probably a phishing scam trying to trick you into downloading malware. The most recent campaign duplicates a trustworthy Office 365 email and can fool even the most skeptical users. Here’s how to stay safe.
Have you ever received an email that claimed to come from a bank or government office when it obviously didn’t? It was probably a phishing scam trying to trick you into downloading malware. The most recent campaign duplicates a trustworthy Office 365 email and can fool even the most skeptical users. Here’s how to stay safe. Anglers catch fish by dangling bait in front of their victims, and hackers use the same strategy to trick your employees. There’s a new phishing scam making the rounds and the digital bait is almost impossible to distinguish from the real thing. Here are the three things to watch out for in Office 365 scams.
Anglers catch fish by dangling bait in front of their victims, and hackers use the same strategy to trick your employees. There’s a new phishing scam making the rounds and the digital bait is almost impossible to distinguish from the real thing. Here are the three things to watch out for in Office 365 scams. More and more small and medium-sized businesses are making the switch from on-premises systems to cloud-hosted Office 365. If you’re one of them, you need to ensure a smooth and secure transition. Here’s what you need to do.
More and more small and medium-sized businesses are making the switch from on-premises systems to cloud-hosted Office 365. If you’re one of them, you need to ensure a smooth and secure transition. Here’s what you need to do. It’s easy to see why Office 365 is an attractive solution for small and medium-sized businesses already familiar with the Office interface. More and more companies are making the move to the cloud, but there are security issues to consider.
It’s easy to see why Office 365 is an attractive solution for small and medium-sized businesses already familiar with the Office interface. More and more companies are making the move to the cloud, but there are security issues to consider. Making the decision to migrate from an on-site system to a cloud-based Office 365 is easy, but the migration process itself presents numerous security challenges. By covering these essentials, you’ll minimize security breaches and ensure you can enjoy the benefits of Office 365.
Making the decision to migrate from an on-site system to a cloud-based Office 365 is easy, but the migration process itself presents numerous security challenges. By covering these essentials, you’ll minimize security breaches and ensure you can enjoy the benefits of Office 365. Cloud computing has proven to be a cost-effective necessity for small businesses. However, there are still many owners who remain misinformed about the intricacies of cloud solutions. Here are some common misconceptions you should stop believing about the cloud.
Cloud computing has proven to be a cost-effective necessity for small businesses. However, there are still many owners who remain misinformed about the intricacies of cloud solutions. Here are some common misconceptions you should stop believing about the cloud.